Federated attributes
Some federated resources require different settings for roles or entitlements to allow your users access and these are usually controlled by permission sets.
If you only have one permission set and need different values for these attributes, you will need to use additional permission sets to give users the other roles and entitlements settings. These additional permission sets do not need to have any resources in them unless you are using MyAthens or restrictive mode, but including resources will not do any harm.
Since you can get statistics reports broken down by permission set, you may already have additional permission sets that group users in useful ways that you can utilise.
The 'Role' attribute
This is used where a service provider uses terms such as Affiliation, Scoped Affiliation or eduPersonScopedAffiliation and basically means a user's role within your organisation. Options are Affiliate, Alum, Employee, Faculty, Library walk-in, Member, Staff & Student and the service provider will use one of those in connection with one of the phrases for role or affiliation.
Select the relevant role from the drop down list and save changes.
The 'Entitlements' attribute
These are not used as often as the role and are specific to individual service providers who will use terms such as entitlement or eduPersonEntitlement to describe them if they need to.
When you click in the box you will be presented with a searchable list of resource names to choose from. Once chosen, you can enter the value or values below it that the service provider specified.
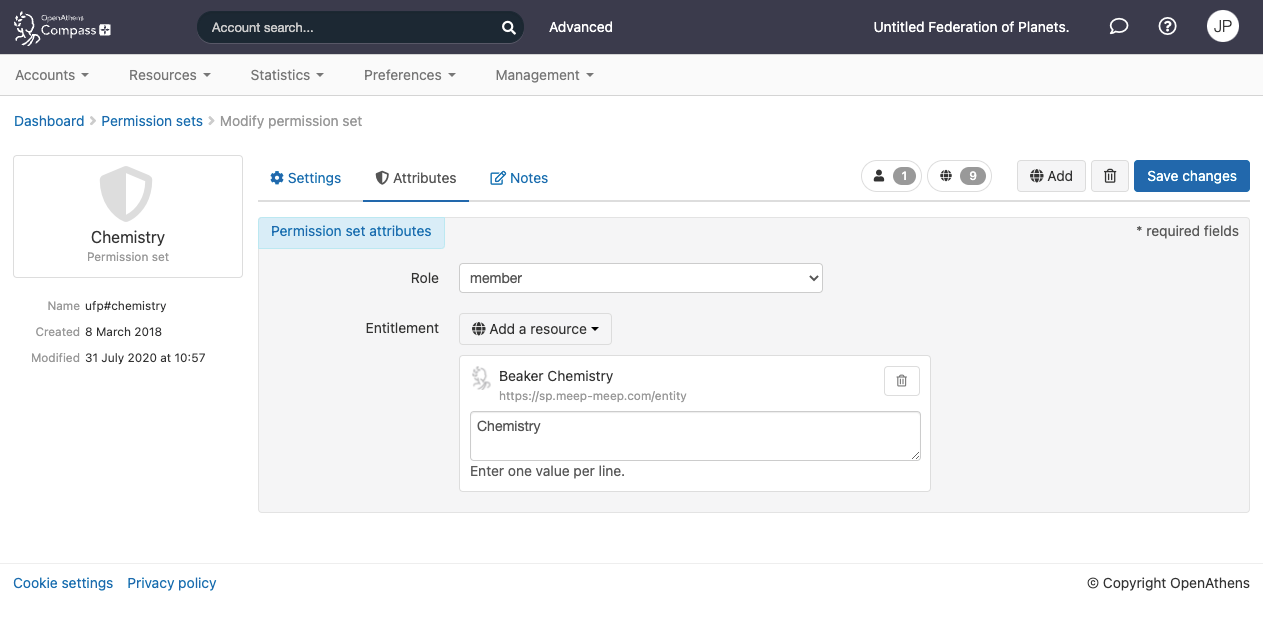
Because the entitlement value is only released to a specified resource, you can add as many resource entitlement values to a permission set as you need to.
With both role and entitlement, they will be passed to service providers for all users who have this permission set, so if they should only be passed for a sub-set of your users you should set them in a permission set that is only allocated to that sub-set.
Anything to watch out for?
Whilst resources could deduce a role of 'member' when they are passed roles such as staff or student, this is not necessarily universal. The solution is to create and apply a permission set with the member attribute to all users.
