Updating metadata or relying party certificates for SAML local connectors
We are updating our signing and encryption certificate within our metadata. If your organisation uses a SAML based local connector to sign users into OpenAthens, you may need to take immediate action to prevent disruption to service.
Updates must be in place before Monday 3 February 2025 for the signing certificate.
If you additionally encrypt responses you will need to update that certificate by Monday 24 February
We periodically have to update the certificate used to secure messages between OpenAthens and SAML based local directory services. Each certificate lasts several years.
In the months before the update takes effect, we’ll contact you about the changes you’ll need to make. When you get such a notice, be sure to pass it to the people who can make the changes. It will probably include a link to this page.
What does your organisation need to do?
The steps you need to take vary between the directory software at your end.
Some do not store the OpenAthens certificate by default, and will not require any action. E.g:
Microsoft Azure/Entra - no action required
Google Workspace - no action required
Okta - no action required
For the rest, including ADFS and Shibboleth, the best option is to consult its documentation to determine how to update the OpenAthens certificate. Terms can vary but might include:
connecting to a service provider
relying party trust
If your system allows you to add the new certificate alongside the outgoing one in your system, you can avoid downtime for your users.
If you encrypt responses you will need to update that certificate too.
Updating the certificate by refreshing the OpenAthens metadata
In many systems you can take care of this just by refreshing the OpenAthens metadata. Your local directory may have stored the URL, but if it has not:
In the OpenAthens administration area https://admin.openathens.net:
Go to Management > Connections
Select your connection
Go to the Relying party tab
Copy the URL for this connections metadata
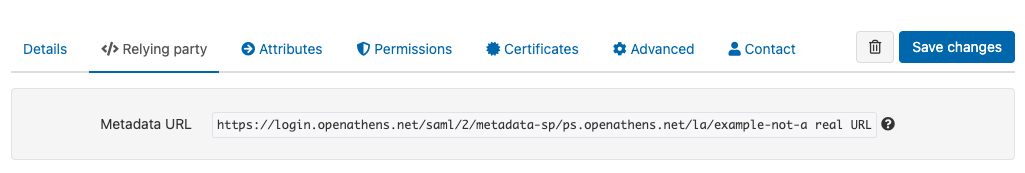
Paste this URL into the metadata address box of your local authentication source. Some sources need you to upload a metadata file instead - in that case go to the URL in a browser and save the page with a .xml extension.
If you have multiple SAML connections, you will need to repeat these steps for every connection.
Updating the certificate manually
In the case of us updating the certificate, we will have told you what the new one is (see below). You can also extract it from the metadata URL described above.
Support
Our service desk are always happy to help but may be busier than usual near to a certificate change.
Old certificate
New certificate details
This certificate example is the one [being] made live on 3 February 2025 12:00 UTC. It will be used for signing and encryption.
Not Before: Apr 9 13:15:36 2024 UTC
Not After : Apr 9 13:15:36 2034 UTC
Serial number: 33e64f9cd5aef2c20b113d3cf08a36c34d80e715
-----BEGIN CERTIFICATE-----
MIID+TCCAuGgAwIBAgIUM+ZPnNWu8sILET088Io2w02A5xUwDQYJKoZIhvcNAQEL
BQAwgYsxCzAJBgNVBAYTAkdCMRkwFwYDVQQIDBBCcmlzdG9sLCBDaXR5IG9mMQ0w
CwYDVQQKDARKaXNjMR8wHQYDVQQDDBZnYXRld2F5Lm9wZW5hdGhlbnMubmV0MTEw
LwYJKoZIhvcNAQkBFiJmZWRlcmF0aW9uLXNlY3VyaXR5QG9wZW5hdGhlbnMubmV0
MB4XDTI0MDQwOTEzMTUzNloXDTM0MDQwOTEzMTUzNlowgYsxCzAJBgNVBAYTAkdC
MRkwFwYDVQQIDBBCcmlzdG9sLCBDaXR5IG9mMQ0wCwYDVQQKDARKaXNjMR8wHQYD
VQQDDBZnYXRld2F5Lm9wZW5hdGhlbnMubmV0MTEwLwYJKoZIhvcNAQkBFiJmZWRl
cmF0aW9uLXNlY3VyaXR5QG9wZW5hdGhlbnMubmV0MIIBIjANBgkqhkiG9w0BAQEF
AAOCAQ8AMIIBCgKCAQEAsc/LNDF5S/9kLO/j/tv/fgLWyf/LUEMrdCE3IFSxLKQc
EBWYzHp9/ihLMIiukHzi/okzdcwp8DObBAs6fRmELzmwZ9ACgDFWu410dYVSI/Bh
BTg7791MzrO8u7bAt4g27QJRP9Akw19ZqytRR8GbC6HYkGXL2b/zOvvmkjtjBZoO
Qy8cd1o65xm6fkfCMDIbYAsxi0UXNBk/lifh/rLLMv7E/WUpCFtw1IDp22g10QCC
Fv4wwPgPTMCgFKtxlsiCe9dYrAaHtAryOJ4GQ242fig0LMU3cRe1Fr/3MSuc0M2B
5mSwHgj/1w5L44X3vg6E91kgtdUjCdbLp0XeMBipDwIDAQABo1MwUTAdBgNVHQ4E
FgQUms57hFh1e+SmuOrSFbOz4PE8nWwwHwYDVR0jBBgwFoAUms57hFh1e+SmuOrS
FbOz4PE8nWwwDwYDVR0TAQH/BAUwAwEB/zANBgkqhkiG9w0BAQsFAAOCAQEAewlr
WYe3uY1UIZ5kd6ZBpFeWuv+N5yzFRSnGkjZyBYZNRuBQdnLadYRWJ8E57e1aDDHT
hrsK8e2aABa7b4uzpeOfiSFW3InPDR/XbAO92xvTGnBisBrOHSXe08gi+cWz0ORc
0wWZmN3fNQyiaDZ1AIirf25E3noetBF4kIDzFs7OLca+pCDfGcj32OEGnDs4h+gF
YfFI87CaEE2tBqqfcpk/ec5LOu7sNHOrBb5f77xwXffoubhSK4QMoUIpWwuL0W7I
/N9rcFL5YjAJ2EKfWbXllAGyDKj9Y+48RdtGK5Sxbfkf4T7utehVerqF2k0IbI+u
E/EFXheIvEglUQpe9w==
-----END CERTIFICATE-----SHA1 fingerprint = A9:91:F3:84:45:47:1C:67:7C:2B:0A:DC:63:83:25:3B:45:3C:47:26
SHA256 fingerprint = 4A:7A:87:11:E6:CC:DD:28:B0:DD:5F:70:F9:9D:1E:0B:33:EB:D0:F8:59:AB:B3:95:91:EA:63:32:AB:5A:3F:35
